PassLeader just published the NEWEST Fortinet NSE4_FGT-7.2 exam dumps! And, PassLeader offer two types of the NSE4_FGT-7.2 dumps — NSE4_FGT-7.2 VCE dumps and NSE4_FGT-7.2 PDF dumps, both VCE and PDF contain the NEWEST NSE4_FGT-7.2 exam questions, they will help you PASSING the Fortinet NSE4_FGT-7.2 exam easily! Now, get the NEWEST NSE4_FGT-7.2 dumps in VCE and PDF from PassLeader — https://www.passleader.com/nse4-fgt-7-2.html (221 Q&As Dumps)
What’s more, part of that PassLeader NSE4_FGT-7.2 dumps now are free — https://drive.google.com/drive/folders/1tn9O9HH_VzMwGLr8JlDSpWJ1OfoQGniZ
NEW QUESTION 204
What are two functions of the ZTNA rule? (Choose two.)
A. It redirects the client request to the access proxy.
B. It applies security profiles to protect traffic.
C. It defines the access proxy.
D. It enforces access control.
Answer: BD
Explanation:
A ZTNA rule is a proxy policy used to enforce access control. You can define ZTNA tags or tag groups to enforce zero-trust role-based access. To create a rule, type a rule name, and add IP addresses and ZTNA tags or tag groups that are allowed or blocked access. You also select the ZTNA server as the destination. You can also apply security profiles to protect this traffic.
NEW QUESTION 205
Which two statements describe how the RPF check is used? (Choose two.)
A. The RPF check is a mechanism that protects FortiGate and the network from IP spoofing attacks.
B. The RPF check is run on the first sent and reply packet of any new session.
C. The RPF check is run on the first sent packet of any new session.
D. The RPF check is run on the first reply packet of any new session.
Answer: AC
Explanation:
The RPF check is a mechanism that protects FortiGate and your network from IP spoofing attacks by checking for a return path to the source in the routing table. FortiGate performs an RPF check only on the first packet of a new session. That is, after the first packet passes the RPF check and FortiGate accepts the session, FortiGate doesn’t perform any additional RPF checks on that session.
NEW QUESTION 206
An organization requires remote users to send external application data running on their PCs and access FTP resources through an SSL/TLS connection. Which FortiGate configuration can achieve this goal?
A. SSL VPN bookmark.
B. SSL VPN tunnel.
C. Zero trust network access.
D. SSL VPN quick connection.
Answer: B
Explanation:
Tunnel mode requires FortiClient to connect to FortiGate. FortiClient adds a virtual network adapter identified as fortissl to the user’s PC. This virtual adapter dynamically receives an IP address from FortiGate each time FortiGate establishes a new VPN connection. Inside the tunnel, all traffic is SSL/TLS encapsulated. The main advantage of tunnel mode over web mode is that after the VPN is established, any IP network application running on the client can send traffic through the tunnel.
NEW QUESTION 207
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
A. Extended authentication (XAuth) for faster authentication because fewer packets are exchanged.
B. Extended authentication (XAuth) to request the remote peer to provide a username and password.
C. No certificate is required on the remote peer when you set the certificate signature as the authentication method.
D. Pre-shared key and certificate signature as authentication methods.
Answer: BD
Explanation:
Authentication-wise, both versions support PSK and certificate signature. Although only IKEv1 supports XAuth, IKEv2 supports EAP, which is equivalent to XAuth.
NEW QUESTION 208
If Internet Service is already selected as Destination in a firewall policy, which other configuration object can be selected for the Destination field of a firewall policy?
A. IP address.
B. No other object can be added.
C. FQDN address.
D. User or User Group.
Answer: B
Explanation:
When configuring your firewall policy, you can use Internet Service as the destination in a firewall policy, which contains all the IP addresses, ports, and protocols used by that service. For the same reason, you cannot mix regular address objects with ISDB objects, and you cannot select services on a firewall policy. The ISDB objects already have services information, which is hardcoded.
NEW QUESTION 209
Which statement is correct regarding the security fabric?
A. FortiManager is one of the required member devices.
B. FortiGate devices must be operating in NAT mode.
C. A minimum of two Fortinet devices is required.
D. FortiGate Cloud cannot be used for logging purposes.
Answer: B
Explanation:
You must have a minimum of two FortiGate devices at the core of the Security Fabric, plus one FortiAnalyzer or cloud logging solution. FortiAnalyzer Cloud or FortiGate Cloud can act as the cloud logging solution. The FortiGate devices must be running in NAT mode.
NEW QUESTION 210
What is a reason for triggering IPS fail open?
A. The IPS socket buffer is full and the IPS engine cannot process additional packets.
B. The IPS engine cannot decode a packet.
C. The IPS engine is upgraded.
D. The administrator enabled NTurbo acceleration.
Answer: A
Explanation:
A fail-open scenario is triggered when IPS raw socket buffer is full. Therefore IPS engine has no space in memory to create more sessions and needs to decide whether to drop the sessions or bypass the sessions without inspection.
NEW QUESTION 211
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
A. VDOMs without ports with connected devices are not displayed in the topology.
B. Downstream devices can connect to the upstream device from any of their VDOMs.
C. Security rating reports can be run individually for each configured VDOM.
D. Each VDOM in the environment can be part of a different Security Fabric.
Answer: A
Explanation:
When you configure FortiGate devices in multi-vdom mode and add them to the Security Fabric, each VDOM with its assigned ports is displayed when one or more devices are detected. Only the ports with discovered and connected devices appear in the Security Fabric view and, because of this, you must enable Device Detection on ports you want to have displayed in the Security Fabric. VDOMs without ports with connected devices are not displayed. All VDOMs configured must be part of a single Security Fabric.
NEW QUESTION 212
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors. What is the reason for the certificate warning errors?
A. The matching firewall policy is set to proxy inspection mode.
B. The certificate used by FortiGate for SSL inspection does not contain the required certificate extensions.
C. The full SSL inspection feature does not have a valid license.
D. The browser does not trust the certificate used by FortiGate for SSL inspection.
Answer: D
Explanation:
If FortiGate receives a trusted SSL certificate, then it generates a temporary certificate signed by the built-in Fortinet_CA_SSL certificate and sends it to the browser. If the browser trusts the Fortinet_CA_SSL certificate, the browser completes the SSL handshake. Otherwise, the browser also presents a warning message informing the user that the site is untrusted. In other words, for this function to work as intended, you must import the Fortinet_CA_SSL certificate into the trusted root CA certificate store of your browser.
NEW QUESTION 213
An employee needs to connect to the office through a high-latency internet connection. Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
A. idle-timeout
B. login-timeout
C. udp-idle-timer
D. session-ttl
Answer: B
Explanation:
When connected to SSL VPN over high latency connections, FortiGate can time out the client before the client can finish the negotiation process, such as DNS lookup and time to enter a token. Two new CLI commands under config vpn ssl settings have been added to address this. The first command allows you to set up the login timeout, replacing the previous hard timeout value. The second command allows you to set up the maximum DTLS hello timeout for SSL VPN connections.
NEW QUESTION 214
Refer to the exhibit:
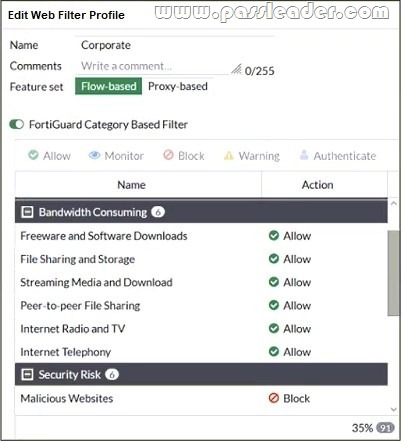
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile. An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category. What are two solutions for satisfying the requirement? (Choose two.)
A. Configure a separate firewall policy with action Deny and an FQDN address object for *.download.com as destination address.
B. Configure a web override rating for download.com and select Malicious Websites as the subcategory.
C. Set the Freeware and Software Downloads category Action to Warning.
D. Configure a static URL filter entry for download.com with Type and Action set to Wildcard and Block, respectively.
Answer: BD
Explanation:
If you want to make an exception, for example, rather than unblock access to a potentially unwanted category, change the website to an allowed category. You can also do the reverse. You can block a website that belongs to an allowed category. Static URL filtering is another web filter feature. Configured URLs in the URL filter are checked against the visited websites. If a match is found, the configured action is taken. URL filtering has the same patterns as static domain filtering: simple, regular expressions, and wildcard.
NEW QUESTION 215
Refer to the exhibits:
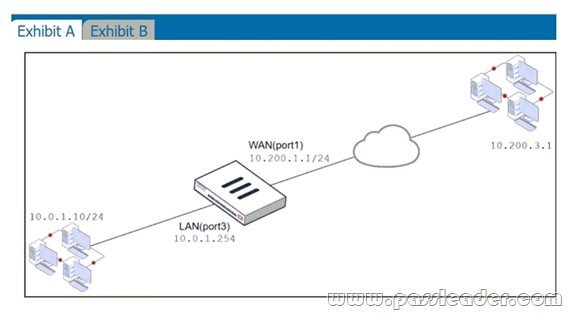
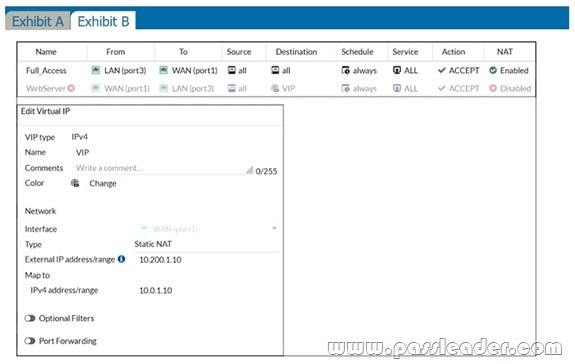
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration. The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port3) interface has the IP address 10.0.1.254/24. The administrator disabled the WebServer firewall policy. Which IP address will be used to source NAT the traffic, if a user with address 10.0.1.10 connects over SSH to the host with address 10.200.3.1?
A. 10.200.1.10
B. 10.0.1.254
C. 10.200.1.1
D. 10.200.3.1
Answer: C
Explanation:
Traffic is coming from LAN to WAN, matches policy Full_Access which has NAT enable, so traffic uses source IP address of outgoing interface. Simple SNAT.
NEW QUESTION 216
An administrator wants to simplify remote access without asking users to provide user credentials. Which access control method provides this solution?
A. ZTNA IP/MAC filtering mode.
B. ZTNA access proxy.
C. SSL VPN.
D. L2TP.
Answer: B
Explanation:
ZTNA access proxy allows users to securely access resources through an SSL-encrypted access proxy. This simplifies remote access by eliminating the use of VPNs.
NEW QUESTION 217
What are two scanning techniques supported by FortiGate? (Choose two.)
A. Machine learning scan.
B. Antivirus scan.
C. Ransomware scan.
D. Trojan scan.
Answer: AB
Explanation:
Like viruses, which use many methods to avoid detection, FortiGate uses many techniques to detect viruses. These detection techniques include:
– Antivirus scan.
– Grayware scan.
– Machine learning (AI) scan.
If all antivirus features are enabled, FortiGate applies the following scanning order: antivirus scan, followed by grayware scan, followed by AI scan.
NEW QUESTION 218
Refer to the exhibit:
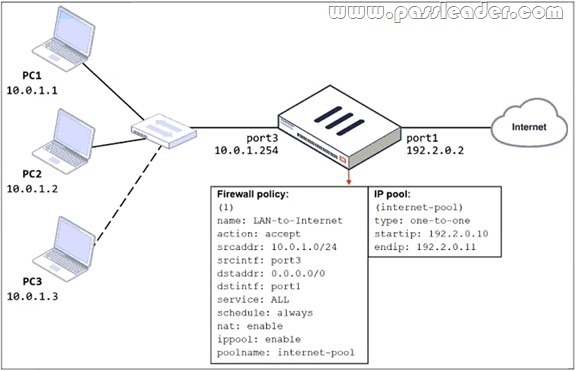
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device. Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet. Based on the information shown in the exhibit, which three configuration changes should the administrator make to fix the connectivity issue for PC3? (Choose three.)
A. In the IP pool configuration, set type to overload.
B. Configure 192.2.0.12/24 as the secondary IP address on port1.
C. In the firewall policy configuration, disable ippool.
D. In the IP pool configuration, set endip to 192.2.0.12.
E. Configure another firewall policy that matches only the address of PC3 as source, and then place the policy on top of the list.
Answer: ACD
NEW QUESTION 219
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
A. System time.
B. FortiGuard update servers.
C. Operating mode.
D. NGFW mode.
Answer: CD
Explanation:
– Operating mode (transparent mode and Nat mode).
– NGFW mode (profile-based, policy-based).
NEW QUESTION 220
How can you disable RPF checking?
A. Disable fail-detect on the interface level settings.
B. Disable strict-src-check under system settings.
C. Unset fail-alert-interfaces on the interface level settings.
D. Disable src-check on the interface level settings.
Answer: D
Explanation:
“config system interface
edit <interface>
set src-check disable
next
end”
NEW QUESTION 221
……
Learning the PassLeader NSE4_FGT-7.2 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/nse4-fgt-7-2.html (221 Q&As Dumps)
BONUS!!! Download part of PassLeader NSE4_FGT-7.2 dumps for free — https://drive.google.com/drive/folders/1tn9O9HH_VzMwGLr8JlDSpWJ1OfoQGniZ