PassLeader just published the NEWEST Fortinet NSE4_FGT-7.2 exam dumps! And, PassLeader offer two types of the NSE4_FGT-7.2 dumps — NSE4_FGT-7.2 VCE dumps and NSE4_FGT-7.2 PDF dumps, both VCE and PDF contain the NEWEST NSE4_FGT-7.2 exam questions, they will help you PASSING the Fortinet NSE4_FGT-7.2 exam easily! Now, get the NEWEST NSE4_FGT-7.2 dumps in VCE and PDF from PassLeader — https://www.passleader.com/nse4-fgt-7-2.html (201 Q&As Dumps –> 221 Q&As Dumps)
What’s more, part of that PassLeader NSE4_FGT-7.2 dumps now are free — https://drive.google.com/drive/folders/1tn9O9HH_VzMwGLr8JlDSpWJ1OfoQGniZ
NEW QUESTION 1
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings. What is true about the DNS connection to a FortiGuard server?
A. It uses UDP 8888.
B. It uses UDP 53.
C. It uses DNS over HTTPS.
D. It uses DNS over TLS.
Answer: B
NEW QUESTION 2
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and does not block the file, allowing it to be downloaded. The administrator confirms that the traffic matches the configured firewall policy. What are two reasons for the failed virus detection by FortiGate? (Choose two.)
A. The website is exempted from SSL inspection.
B. The EICAR test file exceeds the protocol options oversize limit.
C. The selected SSL inspection profile has certificate inspection enabled.
D. The browser does not trust the FortiGate self-signed CA certificate.
Answer: AC
NEW QUESTION 3
Which statement is correct regarding the use of application control for inspecting web applications?
A. Application control can identify child and parent applications, and perform different actions on them.
B. Application control signatures are organized in a nonhierarchical structure.
C. Application control does not require SSL inspection to identify web applications.
D. Application control does not display a replacement message for a blocked web application.
Answer: A
Explanation:
Application control is a feature that allows FortiGate to inspect and control the use of specific web applications on the network. When application control is enabled, FortiGate can identify child and parent applications, and can perform different actions on them based on the configuration.
https://www.fortinetguru.com/2016/06/application-control-fortinet-fortigate/
NEW QUESTION 4
Which timeout setting can be responsible for deleting SSL VPN associated sessions?
A. SSL VPN idle-timeout.
B. SSL VPN http-request-body-timeout.
C. SSL VPN login-timeout.
D. SSL VPN dtls-hello-timeout.
Answer: A
Explanation:
The SSL VPN idle-timeout setting determines how long an SSL VPN session can be inactive before it is terminated. When an SSL VPN session becomes inactive (for example, if the user closes the VPN client or disconnects from the network), the session timer begins to count down. If the timer reaches the idle-timeout value before the user reconnects or sends any new traffic, the session will be terminated and the associated resources (such as VPN tunnels and virtual interfaces) will be deleted.
https://support.sophos.com/support/s/article/KB-000038126
NEW QUESTION 5
What are two functions of ZTNA? (Choose two.)
A. ZTNA manages access through the client only.
B. ZTNA manages access for remote users only.
C. ZTNA provides a security posture check.
D. ZTNA provides role-based access.
Answer: CD
Explanation:
ZTNA (Zero Trust Network Access) is a security architecture that is designed to provide secure access to network resources for users, devices, and applications. It is based on the principle of “never trust, always verify,” which means that all access to network resources is subject to strict verification and authentication. Two functions of ZTNA are:
– ZTNA provides a security posture check: ZTNA checks the security posture of devices and users that are attempting to access network resources. This can include checks on the device’s software and hardware configurations, security settings, and the presence of malware.
– ZTNA provides role-based access: ZTNA controls access to network resources based on the role of the user or device. Users and devices are granted access to only those resources that are necessary for their role, and all other access is denied. This helps to prevent unauthorized access and minimize the risk of data breaches.
https://docs.fortinet.com/document/fortigate/7.0.0/new-features/855420/zero-trust-network-access-introduction
NEW QUESTION 6
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
A. FortiGate uses fewer resources.
B. FortiGate performs a more exhaustive inspection on traffic.
C. FortiGate adds less latency to traffic.
D. FortiGate allocates two sessions per connection.
Answer: AC
Explanation:
Flow-based inspection is a type of traffic inspection that is used by some firewall devices, including FortiGate, to analyze network traffic. It is designed to be more efficient and less resource-intensive than proxy-based inspection, and it offers several benefits over this approach. Two benefits of flow-based inspection compared to proxy-based inspection are:
– FortiGate uses fewer resources: Flow-based inspection uses fewer resources than proxy-based inspection, which can help to improve the performance of the firewall device and reduce the impact on overall system performance.
– FortiGate adds less latency to traffic: Flow-based inspection adds less latency to traffic than proxy-based inspection, which can be important for real-time applications or other types of traffic that require low latency.
https://www.fortinetguru.com/2018/09/fortios-6-inspection-modes/
https://community.fortinet.com/t5/Support-Forum/Proxy-based-vs-Flow-based-Inspection-Mode-for-Web-Filter/m-p/19204
NEW QUESTION 7
Which statement correctly describes the use of reliable logging on FortiGate?
A. Reliable logging is enabled by default in all configuration scenarios.
B. Reliable logging is required to encrypt the transmission of logs.
C. Reliable logging can be configured only using the CLI.
D. Reliable logging prevents the loss of logs when the local disk is full.
Answer: D
Explanation:
On a FortiGate device, reliable logging is a feature that helps to prevent the loss of log messages when the local disk is full. When reliable logging is enabled, the FortiGate will store log messages in a buffer until they can be written to the local disk. This helps to ensure that log messages are not lost due to a full disk, allowing administrators to maintain an accurate record of activity on the network. Reliable logging is not enabled by default in all configuration scenarios, and it does not encrypt the transmission of logs or require the use of the CLI to be configured. However, it is a useful feature to enable in order to maintain a comprehensive record of activity on the network and help with troubleshooting and security analysis.
https://docs.fortinet.com/document/fortigate/7.2.0/new-features/942202/improve-fortianalyzer-log-caching
NEW QUESTION 8
Which downstream FortiGate VDOM is used to join the Security Fabric when split-task VDOM is enabled on all FortiGate devices?
A. Root VDOM
B. FG-traffic VDOM
C. Customer VDOM
D. Global VDOM
Answer: A
NEW QUESTION 9
Which two statements are correct about NGFW Policy-based mode? (Choose two.)
A. NGFW policy-based mode does not require the use of central source NAT policy.
B. NGFW policy-based mode can only be applied globally and not on individual VDOMs.
C. NGFW policy-based mode supports creating applications and web filtering categories directly in a firewall policy.
D. NGFW policy-based mode policies support only flow inspection.
Answer: CD
Explanation:
https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/38324/ngfw-policy-based-mode
NEW QUESTION 10
Which two statements are correct about a software switch on FortiGate? (Choose two.)
A. It can be configured only when FortiGate is operating in NAT mode.
B. Can act as a Layer 2 switch as well as a Layer 3 router.
C. All interfaces in the software switch share the same IP address.
D. It can group only physical interfaces.
Answer: AC
NEW QUESTION 11
Which two statements are true about collector agent advanced mode? (Choose two.)
A. Advanced mode uses Windows convention–NetBios: Domain\Username.
B. FortiGate can be configured as an LDAP client and group filters can be configured on FortiGate.
C. Advanced mode supports nested or inherited groups.
D. Security profiles can be applied only to user groups, not individual users.
Answer: BC
Explanation:
https://docs.fortinet.com/document/fortigate/6.0.0/handbook/482937/agent-based-fsso
NEW QUESTION 12
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not. Which configuration option is the most effective way to support this request?
A. Implement a web filter category override for the specified website.
B. Implement a DNS filter for the specified website.
C. Implement web filter quotas for the specified website.
D. Implement web filter authentication for the specified website.
Answer: A
NEW QUESTION 13
An administrator has a requirement to keep an application session from timing out on port 80. What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.)
A. Create a new firewall policy with the new HTTP service and place it above the existing HTTP policy.
B. Create a new service object for HTTP service and set the session TTL to never.
C. Set the TTL value to never under config system-ttl.
D. Set the session TTL on the HTTP policy to maximum.
Answer: BC
NEW QUESTION 14
In which two ways can RPF checking be disabled? (Choose two.)
A. Enable anti-replay in firewall policy.
B. Disable the RPF check at the FortiGate interface level for the source check.
C. Enable asymmetric routing.
D. Disable strict-arc-check under system settings.
Answer: BC
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-disable-Reverse-Path-Forwarding-RPF-per/ta-p/193338?externalID=FD51279
NEW QUESTION 15
Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
A. diagnose sys top
B. execute ping
C. execute traceroute
D. diagnose sniffer packet any
E. get system arp
Answer: BCD
NEW QUESTION 16
Which two statements are true about the RPF check? (Choose two.)
A. The RPF check is run on the first sent packet of any new session.
B. The RPF check is run on the first reply packet of any new session.
C. The RPF check is run on the first sent and reply packet of any new session.
D. RPF is a mechanism that protects FortiGate and your network from IP spoofing attacks.
Answer: AD
Explanation:
https://www.programmersought.com/article/16383871634/
NEW QUESTION 17
An administrator needs to configure VPN user access for multiple sites using the same soft FortiToken. Each site has a FortiGate VPN gateway. What must an administrator do to achieve this objective?
A. The administrator can register the same FortiToken on more than one FortiGate.
B. The administrator must use a FortiAuthenticator device.
C. The administrator can use a third-party radius OTP server.
D. The administrator must use the user self-registration server.
Answer: B
NEW QUESTION 18
Which three methods are used by the collector agent for AD polling? (Choose three.)
A. FortiGate polling.
B. NetAPI.
C. Novell API.
D. WMI.
E. WinSecLog.
Answer: BDE
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Comparison-between-DC-Agent-mode-and-polling-mode/ta-p/194621?externalID=FD47732
NEW QUESTION 19
Which two statements are correct about SLA targets? (Choose two.)
A. You can configure only two SLA targets per one Performance SLA.
B. SLA targets are optional.
C. SLA targets are required for SD-WAN rules with a Best Quality strategy.
D. SLA targets are used only when referenced by an SD-WAN rule.
Answer: BD
NEW QUESTION 20
Which two types of traffic are managed only by the management VDOM? (Choose two.)
A. FortiGuard web filter queries
B. PKI
C. Traffic shaping
D. DNS
Answer: AD
Explanation:
NTP, FortiGuard updated/queries, SNMP, DNS Filtering, Log settings and other mgmt related services.
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Management-VDOM-should-have-Internet-connection/ta-p/198606?externalID=FD46542
https://docs.fortinet.com/document/fortigate/7.2.3/administration-guide/597696/vdom-overview
NEW QUESTION 21
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
A. The subject field in the server certificate.
B. The serial number in the server certificate.
C. The server name indication (SNI) extension in the client hello message.
D. The subject alternative name (SAN) field in the server certificate.
E. The host field in the HTTP header.
Answer: ACD
Explanation:
https://checkthefirewall.com/blogs/fortinet/ssl-inspection
NEW QUESTION 22
How does FortiGate act when using SSL VPN in web mode?
A. FortiGate acts as an FDS server.
B. FortiGate acts as an HTTP reverse proxy.
C. FortiGate acts as DNS server.
D. FortiGate acts as router.
Answer: B
Explanation:
https://pub.kb.fortinet.com/ksmcontent/Fortinet-Public/current/Fortigate_v4.0MR3/fortigate-sslvpn-40-mr3.pdf
NEW QUESTION 23
Which security feature does FortiGate provide to protect servers located in the internal networks from attacks such as SQL injections?
A. Denial of Service.
B. Web application firewall.
C. Antivirus.
D. Application control.
Answer: B
Explanation:
https://docs.fortinet.com/document/fortiweb/6.3.3/administration-guide/60895/introduction
NEW QUESTION 24
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
A. FortiGuard web filter cache.
B. FortiGate hostname.
C. NTP.
D. DNS.
Answer: CD
NEW QUESTION 25
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
A. FortiGate automatically negotiates different local and remote addresses with the remote peer.
B. FortiGate automatically negotiates a new security association after the existing security association expires.
C. FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
D. FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
Answer: B
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Using-the-IPSec-auto-negotiate-and-keepalive/ta-p/189536?externalID=12069
NEW QUESTION 26
Refer to the exhibit:
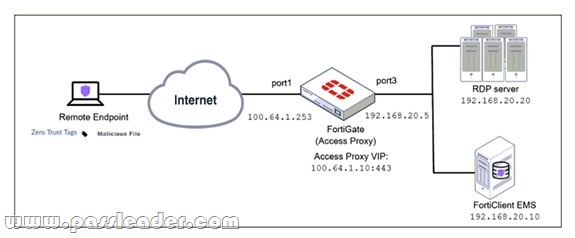
Based on the ZTNA tag, the security posture of the remote endpoint has changed. What will happen to endpoint active ZTNA sessions?
A. They will be re-evaluated to match the endpoint policy.
B. They will be re-evaluated to match the firewall policy.
C. They will be re-evaluated to match the ZTNA policy.
D. They will be re-evaluated to match the security policy.
Answer: C
Explanation:
https://docs.fortinet.com/document/fortigate/7.0.0/new-features/580880/posture-check-verification-for-active-ztna-proxy-session-7-0-2
NEW QUESTION 27
Refer to the exhibit:
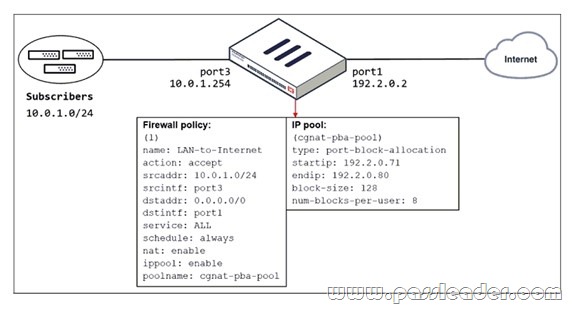
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device. Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
A. FortiGate allocates port blocks per user, based on the configured range of internal IP addresses.
B. FortiGate allocates port blocks on a first-come, first-served basis.
C. FortiGate generates a system event log for every port block allocation made per user.
D. FortiGate allocates 128 port blocks per user.
Answer: AD
NEW QUESTION 28
Refer to the exhibit:
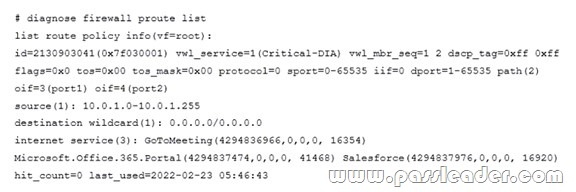
The exhibit shows the output of a diagnose command. What does the output reveal about the policy route?
A. It is an ISDB route in policy route.
B. It is a regular policy route.
C. It is an ISDB policy route with an SDWAN rule.
D. It is an SDWAN rule in policy route.
Answer: C
NEW QUESTION 29
……
Learning the PassLeader NSE4_FGT-7.2 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/nse4-fgt-7-2.html (201 Q&As Dumps –> 221 Q&As Dumps)
BONUS!!! Download part of PassLeader NSE4_FGT-7.2 dumps for free — https://drive.google.com/drive/folders/1tn9O9HH_VzMwGLr8JlDSpWJ1OfoQGniZ